Below is described how to setup pi-hole and OpenDNS at home. I used Raspberry Pi 3 for it and the below tutorial will describe all the steps pertaining to it only. Refer to the end of the blog for additional help.
Prerequisite:
- Raspberry Pi (3 or above) with Raspbian installed and SSH ready. (Refer References section below for help with it. I will call Raspberry Pi as the pi machine henceforth).
- A router supporting custom DHCP configuration (I am going to explain for Netgear Router).
- Computer to SSH the pi machine (Mac or PC) (I used Mac in this tutorial. You can skip this and do it directly on the pi machine if you have set it up with keyboard and monitor).
- Internet
- Lots of spare time. (This is very important)
Step1: Install pi-hole on Raspberry Pi
* Before you begin, ensure that the pi machine is connected to the internet.
- Open Terminal and SSH to the raspberry pi using the command below:
ssh user@pihostname.local
Replace user and pihostname with the user and hostname you have configured for your pi machine.
- On the terminal, type the below commands to install pi-hole.
* Before you begin:
- Use all the default configurations as shown by the installer do not change it (We will change it later using the pi-hole console).
- The installer will ask you to install a webserver to install the pi-hole console. This is an optional step but go ahead with installing it as we need this console later for changing settings of pi-hole.
- Ensure that you do not have another web server on your pi machine. If you have it then the pi-hole console will not come up. So, it is better to stop the server before starting.
- After the installation note the following:
- IPv4 address of the pi machine.
- IPv6 address of the pi machine.
- The password of the pi-hole console given.
- Use all the default configurations as shown by the installer do not change it (We will change it later using the pi-hole console).
- The installer will ask you to install a webserver to install the pi-hole console. This is an optional step but go ahead with installing it as we need this console later for changing settings of pi-hole.
- Ensure that you do not have another web server on your pi machine. If you have it then the pi-hole console will not come up. So, it is better to stop the server before starting.
- After the installation note the following:
- IPv4 address of the pi machine.
- IPv6 address of the pi machine.
- The password of the pi-hole console given.
git clone --depth 1 https://github.com/pi-hole/pi-hole.git Pi-holecd "Pi-hole/automated install/"sudo bash basic-install.shStep2: Configure the pi machine as the DHCP server on Router.
*Before you start, note:
- The configuration below is only for Netgear routers. For other routers, refer to the router manual.
- Ensure Parental Settings are turned off. (Don't worry as after OpenDNS configuration those will get auto applied)
- Go to router admin settings. On Netgear routers, it can be opened in a browser by typing the following URL and entering the admin user password you used while setting up your router. If you did not configure the new admin password then it can be found on your router or in the user manual.
http://routerlogin.net (Ensure that you are connected to your home wifi before opening the URL)
- Change Domain Name Server (DNS) Address settings
- Go to Advanced -> Setup -> Internet Setup
- On the right pane, enter the IPv4 address of the pi machine you noted in Step 1 as Primary DNS after selecting the "Use These DNS Servers" option.
- Apply the settings (This will restart the router)
- Go to Advanced -> Setup -> Internet Setup
- On the right pane, enter the IPv4 address of the pi machine you noted in Step 1 as Primary DNS after selecting the "Use These DNS Servers" option.
- Apply the settings (This will restart the router)
- Change IPv6 settings
- After router is restarted, go to Advanced -> Advanced Setup -> IPv6
- Select "Use DHCP Server"
- Enter the IPv6 address of the pi machine in "Start Address" field
- Select "Use These DNS Servers" option.
- Enter the IPv6 address of the pi machine in "Primary DNS" fields.
- Apply the settings (This will restart the router)
- After router is restarted, go to Advanced -> Advanced Setup -> IPv6
- Select "Use DHCP Server"
- Enter the IPv6 address of the pi machine in "Start Address" field
- Select "Use These DNS Servers" option.
- Enter the IPv6 address of the pi machine in "Primary DNS" fields.
- Apply the settings (This will restart the router)
Step3: Open the pi-hole console and configure OpenDNS
- Open the browser on the computer from which you are doing SSH and enter the following URL
http://pi.hole/admin/index.php?login
or
http://<Ip address of pi machine>/admin/index.php?login
http://pi.hole/admin/index.php?login
or
http://<Ip address of pi machine>/admin/index.php?login
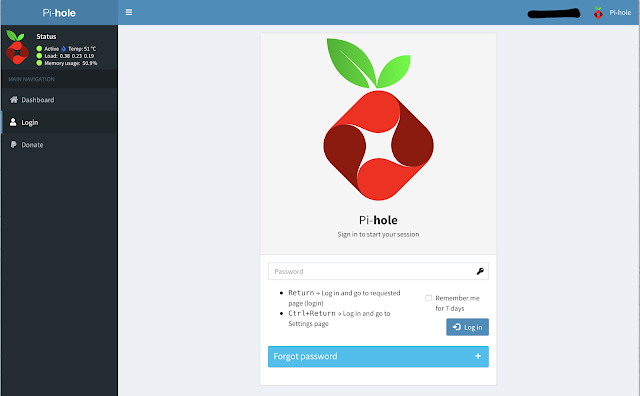
Pi-console will be shown as below:
If you have done everything as described above then you are all set. This not only removes ads from all the apps (on phones) but from all the sites your surf. Plus, you get content filtering from OpenDNS (restricted access to porn, malware, unfriendly sites, etc).
- Enter the password noted in Step 1 and go to Dashboard. The screen will look as shown below
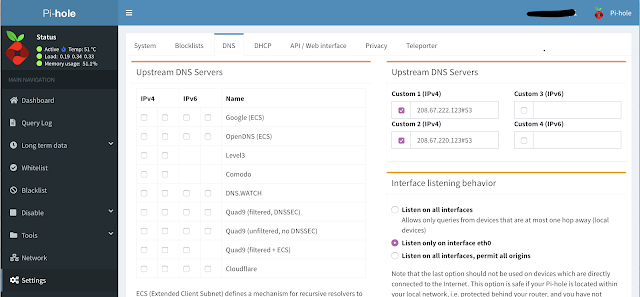
- Go to Settings -> DNS and do the following:
- Uncheck any checkbox under settings "Upstream DNS Servers" on the left side.
- Under "Upstream DNS Servers" on the right side check all the checkboxes and enter the following information:
- Under Custom 1 (IPv4) enter: 208.67.222.123
- Under Custom 2 (IPv4) enter: 208.67.220.123
*Note: Refer IP Addresses at https://docs.pi-hole.net/guides/upstream-dns-providers/ under the OpenDNS section if the above IP address does not work. I chose IP Address with Family Filters (IPv6 server is not present currently).
- After entering the information scroll to the bottom of the page and press the "SAVE" button.
- After you save the information, the screen will look as shown below.
- Uncheck any checkbox under settings "Upstream DNS Servers" on the left side.
- Under "Upstream DNS Servers" on the right side check all the checkboxes and enter the following information:
- Under Custom 1 (IPv4) enter: 208.67.222.123
- Under Custom 2 (IPv4) enter: 208.67.220.123
- After entering the information scroll to the bottom of the page and press the "SAVE" button.
If you have done everything as described above then you are all set. This not only removes ads from all the apps (on phones) but from all the sites your surf. Plus, you get content filtering from OpenDNS (restricted access to porn, malware, unfriendly sites, etc).
References:
- https://projects.raspberrypi.org/en/projects/raspberry-pi-setting-up (Setup Raspberry Pi)
- https://magpi.raspberrypi.org/articles/ssh-remote-control-raspberry-pi (Setup SSH on Raspberry Pi)
- https://pi-hole.net
- https://github.com/pi-hole/pi-hole/#alternative-install-methods
- https://discourse.pi-hole.net/t/how-do-i-configure-my-devices-to-use-pi-hole-as-their-dns-server/245
- https://docs.pi-hole.net/guides/upstream-dns-providers/
- https://discourse.pi-hole.net/t/using-netgear-nighthawk-ac1900-r7000-router-with-opendns-parental-controls-plus-pi-hole/9274/2